Microsoft Windows Credential Guard
What is Microsoft Windows Credential Guard?
Microsoft Windows Credential Guard is a security feature in Microsoft Windows operating system (OS) that isolates user credentials, such as login information, from the rest of the OS. Its purpose is to prevent common credential theft attacks, such as pass the hash and pass the ticket.
Microsoft introduced Credential Guard in Windows 10 Enterprise and Windows Server 2016. It is enabled by default on all systems running on Windows 11, version 22H2 and later. The default enablement is without a Unified Extensible Firmware Interface (UEFI) lock, so Credential Guard can also be disabled remotely by administrators.
Currently, Credential Guard is available in all these Windows systems:
The primary role of Credential Guard is to protect NT LAN Manager (NTLM) password hashes, Kerberos Ticket Granting Tickets (TGTs), and domain credentials -- credentials stored by applications -- in order to prevent credential theft attacks.
When Credential Guard is active, only privileged system software can access domain credentials, NTLM password hashes -- the practice of transforming a character string or key into a new value -- and TGTs. It is particularly effective against pass-the-hash attacks. Additionally, it stores randomized full-length hashes to fight back against trial-and-error threats such as brute-force attacks.
How Microsoft Credential Guard works
Credential Guard uses hardware-backed, virtualization-based security (VBS) and a Local Security Authority (LSA) to store "secrets," i.e., credentials in protected containers. Containers are isolated environments separate from the OS. Here, "separate" means that the containers, and the credentials stored in them, are not accessible to the rest of the OS.
Also, the LSA uses remote procedure calls (RPC) to communicate with the isolated LSA process (a component that stores and protects secrets) and validates each binary before it launches a file inside the protected area. These binaries, which are needed for security, are hosted in the isolated LSA process, and they are signed with a certificate that VBS trusts. This entire system ensures that signatures are validated before the file is launched in the protected environment and helps protect credentials against theft. As a result, even if malware or some other malicious attack penetrates an organization's network, the information protected by Credential Guard can remain safe from theft.

Benefits and drawbacks of Credential Guard
One of the primary benefits of Credential Guard is that it provides robust hardware security via Secure Boot and virtualization to protect credentials and prevent credential theft attacks. All secrets, including NTLM hashes and Kerberos-derived credentials, run in a protected environment that is isolated from the running OS so only privileged system software can access them.
Another benefit of Credential Guard is that it can block many types of targeted attacks and protect organizations from sophisticated techniques and tools.
Its benefits notwithstanding, organizations and security administrators should not assume that Credential Guard is sufficient to protect credentials stored. For example, Credential Guard cannot protect credentials stored and managed by software outside of Windows feature protection or credentials stored by local accounts, Microsoft accounts, keyloggers, and third-party security packages. Credential Guard also cannot prevent credential theft by physical attacks and cannot protect the Active Directory (AD) database running on Windows Server domain controllers. In virtual machines (VMs), Credential Guard cannot provide protection from privileged system attacks originating from the host.
For all these reasons, organizations should implement a multi-layered security architecture, of which Credential Guard is but one part. This architecture must include multiple strategies as well as strong authentication methods like Windows Hello for Business, FIDO 2 security keys, and/or smart cards. Such an architecture is essential to keep persistent threat attacks and new attack techniques at bay.
Credential Guard system requirements
To use Credential Guard, the system must run a Windows edition that supports the following features:
- Windows Enterprise
- Windows Education
Credential Guard will not work on these Windows editions:
- Windows Pro
- Windows Pro Education/SE
For Credential Guard to operate, the device must support VBS and have secure boot functions. VBS uses hardware virtualization and the Windows hypervisor to create an isolated virtual environment for credentials. The secure boot function ensures that the system firmware finds the OS bootloader and examines its digital signature to verify that it hasn't been modified and can therefore be trusted.
To provide robust protection for credentials, Credential Guard must be enabled before a device is joined to a domain (if it is not already). If it is enabled after the device joins a domain, its secrets may already be compromised and may be vulnerable to theft.
In addition to VBS and Secure Boot, Microsoft recommends that organizations use Trusted Platform Module (TPM) version 1.0 or 2.0 and UEFI lock. TPM provides binding to hardware and UEFI lock prevents unauthorized users, including attackers, from making registry key changes to disable Credential Guard.
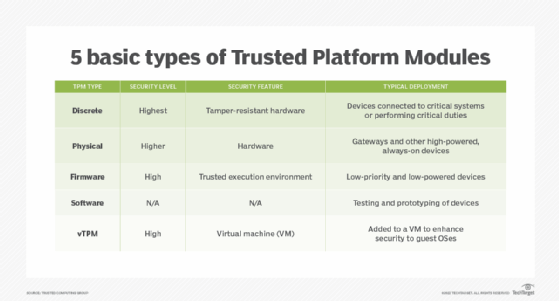
If Credential Guard is to run in Hyper-V VMs, two requirements must be met. One, the Hyper-V host must have an Input-Output Memory Management Unit (IOMMU) that connects an I/O bus capable of direct-memory access to system memory and also maps virtual addresses to physical addresses. The virtual addresses must be device-visible. The second requirement is that the Hyper-V VMs must be generation 2 because Credential Guard is not available for Hyper-V generation 1 VMs.
Administrators should also check their applications' authentication requirements before running Credential Guard. This step is important because enabling Credential Guard blocks some authentication capabilities, including Kerberos Data Encryption Standard encryption support and NTLMv1, which can cause the applications that need these capabilities to break.
Learn how to use Windows Server 2022 secured-core server features and how to enable Windows Defender Device Guard. Compare endpoint detection and response tools for Windows Server.




