Risk Management Framework (RMF)
What is the Risk Management Framework (RMF)?
The Risk Management Framework is a template and guideline used by companies to identify, eliminate and minimize risks. It was originally developed by the National Institute of Standards and Technology to help protect the information systems of the United States government.
The RMF was initially designed for use by federal agencies but can be easily adopted by organizations operating in the private sector. Businesses cannot exist without exposing themselves to risks such as IT problems, litigation and loss of capital. While it is impossible to eliminate all risks involved in running a business, they can be minimized.
What are the components of the RMF?
There are five components that make up the RMF: identification; measurement and assessment; mitigation; reporting and monitoring; and governance.
1. Identification
The first component in implementing the Risk Management Framework is to identify the risks that the organization faces. These might include strategic, legal, operational and privacy risks.
This article is part of
What is risk management and why is it important?
It is important to note that risk identification is not a one-time process. The risks that an organization faces tend to change over time, so risk assessments will need to be performed on a periodic basis.
2. Measurement and assessment
The goal behind the measurement and assessment component is to create a risk profile for each risk that has been identified. There are any number of different ways that organizations might complete the measurement and assessment phase of the process. In some cases, risk measurement might be based on something as simple as how much capital could potentially be lost as a result of the risk. However, in other cases, measuring the potential impact of a risk might be far more difficult. In the field of information security, for example, an organization might attempt to quantify the cost of a security breach compared with the cost of implementing a security mechanism that can help to mitigate the risk.
3. Mitigation
Risk mitigation involves examining the risks that have been identified and determining which risks can and should be eliminated, as opposed to the risks that are deemed to be acceptable.
Part of this process involves coming up with mitigation strategies, such as cyber insurance. For example, if an organization identifies cybersecurity risks that need to be dealt with, then it might choose to integrate security controls into its development lifecycle. Such an organization would likely also put additional baseline security controls in place.
4. Reporting and monitoring
The fourth component in the process is risk reporting and monitoring. This essentially means regularly reexamining the risks in order to make sure that the risk mitigation strategies the organization has adopted are leading to the desired effect.
5. Governance
The last component in the process is risk governance. Risk governance is the process of making sure that the risk mitigation techniques that have been adopted are put into place and that the employees adhere to those policies.
What are the steps of the Risk Management Framework?
According to the National Institute of Standards and Technology, the following seven steps make up the RMF.
1. Prepare
The preparation stage of the RMF focuses on getting the organization ready to adopt a formalized risk management strategy. This might include identifying organizational risks and determining key risk-management roles.
2. Categorize
The categorize stage is where organizations begin assessing the risks that have been identified. This can mean assessing the impact of the various risks and prioritizing the risks that need to be addressed.
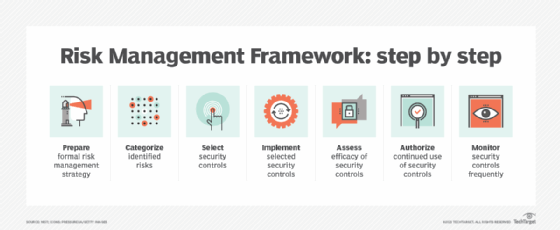
3. Select
The select stage involves choosing the controls that will be used to protect affected systems to minimize or mitigate the risks that have been identified. These controls will vary widely from one system to the next. They might include anything from adopting monitoring solutions to shaping policies that will help to alleviate concerns.
4. Implement
Once an organization has selected the controls it will adopt as part of its risk mitigation strategy, the next stage is implementation. This is where the selected controls are put into place in an effort to head off risks that might exist.
5. Assess
The assess stage comes after the implementation of any selected controls. It seeks to determine whether the selected controls were implemented correctly and if those controls are delivering the desired result. This means making sure any mechanisms that have been implemented are reducing risks in a quantifiable way without accidentally introducing new risks in the process.
6. Authorize
In some instances, the authorize stage is tied to executive approval of the risk mitigation mechanisms that have been put into place. More often, however, the authorize phase is an overview by senior members of the organization who are looking to make sure that risk mitigation strategies are working and that those strategies adhere to any applicable laws and policies that might exist within the organization.
7. Monitor
The monitor phase is designed to provide situational awareness on an ongoing basis. Organizations should continuously evaluate their risk mitigation strategies to ensure they continue to work as intended.
What are the business benefits of an RMF?
The concept of an RMF was initially intended for use by federal organizations, especially with regard to federal information systems. Even so, private sector companies and nonprofit organizations have found the concept of an RMF to be useful. An RMF can help an organization to reduce its risks, thereby minimizing legal exposure and helping to maximize profitability.
Brien Posey is a 15-time Microsoft MVP with two decades of IT experience. He has served as a lead network engineer for the U.S. Department of Defense and as a network administrator for some of the largest insurance companies in America.





