tunneling or port forwarding
What is tunneling or port forwarding?
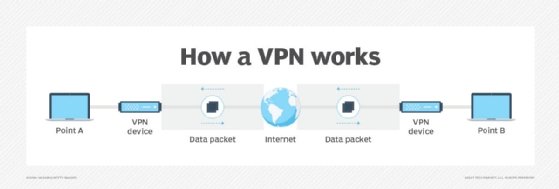
Tunneling or port forwarding is the transmission of data intended for use only within a private -- usually corporate -- network through a public network in such a way that the public network's routing nodes are unaware that the transmission is part of a private network. It enables the use of the internet, which is a public network, to convey data on behalf of a private network.
Exploring the concept of tunneling
Tunneling is redirecting network traffic from one port to another to enable secure access to network traffic and services across firewalls and also from outside the network. Simply put, tunneling is a port redirection technique in which traffic is received at one port and forwarded to another port. It is often done by encapsulating the private network data and protocol information within the public network so that the latter can convey data on behalf of the former. There are several tunneling protocols in use today, such as Generic Routing Encapsulation (GRE).
Generic Routing Encapsulation
GRE is another commonly used tunneling protocol. It was developed by Cisco. In GRE, data packets that use one routing protocol are wrapped or encapsulated within other packets that use another supported protocol. Such encapsulation, which is a form of tunneling, gives the protocol its name.
GRE helps to simplify connections between separate networks by setting up a direct point-to-point connection. Through encapsulation, a packet can cross a network it is not able to cross otherwise. One example is when packets need to travel between local area networks (LANs) in two different physical locations. Even if both LANs support the same protocol -- e.g., IPv6 -- the traffic may have to pass through another third-party network to get from one LAN to another. This third-party network may support a different protocol -- e.g., IPv4. GRE addresses this mismatch by encapsulating IPv6 packets within IPv4 packets, which enables the IPv6 packets to move from LAN1 to LAN2 through the third-party network.
What is SSH tunneling?
In SSH tunneling or SSH port forwarding, an encrypted SSH connection is created between a client and server -- or a local and remote host. Services ports can be relayed through this connection. SSH gets a service request from the client machine and creates a connection to communicate that request to the server machine. The client's request is decrypted and then sent to the server. SSH tunneling can only be used if both the client and server have SSH set up.
SSH tunneling is commonly used to go through firewalls. System administrators (sys admins) -- and cyberattackers -- also use it to open backdoors into the internal network from remote locations.
There are three types of SSH tunneling.
1. Local port forwarding
Local port forwarding is meant to forward a port from the SSH client to the server to make remote resources, which may be on an internal network or behind a firewall, locally available. First, the client listens for connections on a configured port. When it receives a connection, it forwards the connection -- i.e., tunnels the connection -- to an SSH server, which then connects to a configured destination port.
In OpenSSH, local port forwarding is configured using this syntax:
ssh -L 80:intra.example.com:80 gw.example.com
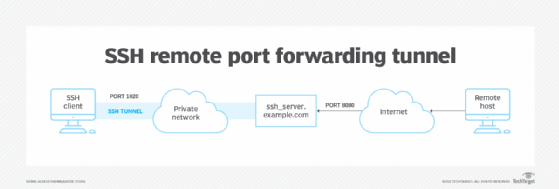
2. Remote port forwarding
Remote port forwarding is a way to access local resources remotely. Thus, when remote forwarding is set up, anyone on the remote server can connect to the configured TCP port -- e.g., 8080 -- on the remote server. The technique is useful when an employee is restricted from remotely accessing office systems or internal web servers.
In OpenSSH, remote SSH port forwarding is configured using this syntax:
ssh -R 8080:localhost:80 public.example.com
3. Dynamic port forwarding
The chief purpose of dynamic port forwarding is to tunnel multiple ports and enable communications across them. In this case, SSH acts like a proxy server. This server is a local (SSH client) machine. When a client connects to this machine, the connection is first forwarded to the remote (SSH server) machine and then to a dynamic port on the destination machine. By using this method, all machines connect to the SSH server, which then forwards the traffic to its destination.
In Linux, macOS and other Unix systems, dynamic port forwarding is configured using this syntax:
ssh -D [LOCAL_IP:]LOCAL_PORT [USER@]SSH_SERVER
The benefits of tunneling
The main benefit of tunneling is that it enables users to securely access network traffic across firewalls. Organizations can use tunneling to set up VPN connections and enable users to access enterprise data from a secure location, even if a firewall is present.
With SSH tunneling, the SSH tunnel enables the transfer of data to remote systems, while circumventing standard firewall security protocols. The SSH tunnels are secure, protecting the data in transit from eavesdropping or other undesirable situations.
Local port forwarding is particularly useful since it enables remote users to connect to services and files on an internal network from outside the network. Similarly, remote forwarding is useful to give an authorized user access to an internal web server from outside. That said, attackers can also use remote forwarding to expose an internal web application and its associated data to the public internet. For this reason, sys admins and IT teams should be careful about configuring tunnels and allowing remote users to access local enterprise systems through these tunnels.
SSH tunneling takes the secure application protocol to the next level for bypassing firewalls and creating secure connections. See how SSH tunneling can be used for both good and evil. Also, check out this glossary of the VPN terminology you need to know.




